In my new role on the Microsoft FastTrack for Azure team I need to be at least 100- to 200-level deep in all of the Azure features. During my ramp-up process I've decided to add items I've found interesting or helpful to my blog hoping that it may help folks starting out on their Azure journey.
NOTE: Azure changes often, so please check out the links in each post to get the latest info on these tidbit topics.
Separate RBAC for management and data access
In Azure Role-based Access Control (RBAC) you set permissions on who can manage a resource, say a Storage account, using RBAC on that resource. So when you give someone permission to manage that storage account, they can create, modify, and delete blob containers within the account. That's about as far as management permissions go though. The management access provided doesn't give the user rights to look at the data within the blobs. If you want someone to be able to read the data you need to add an additional set of entries into the role definition assigned to that user.
The example below is liberally lifted from the Azure docs.
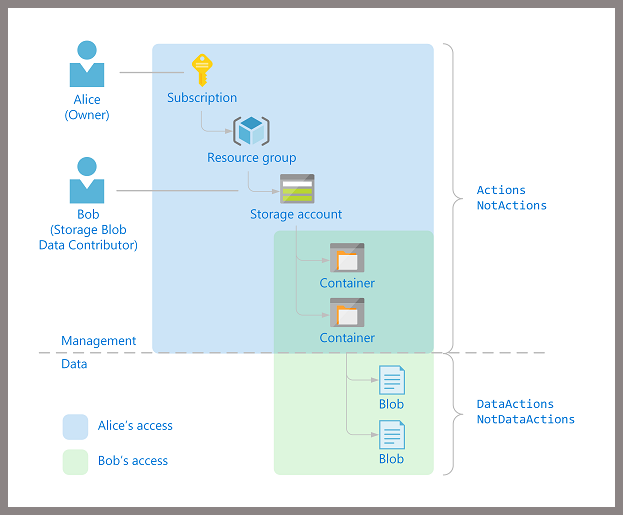
from Microsoft docs: Azure RBAC management and data operations (Preview)
Alice and Bob work together in the IT group. Alice manages the Azure subscription and Bob manages the data for a given application. The company has a "least privilege" policy based on job functions.
Alice is part of IT Operations and needs to be able to manage all the Azure resources in the subscription but she doesn't have a need to look at the data for any of the company's applications.
Bob is part of an application team and needs to manage the application's data that is stored in Azure. He needs to be able to look at the data for the application but he doesn't have rights to edit or delete the blob container the data resides within.
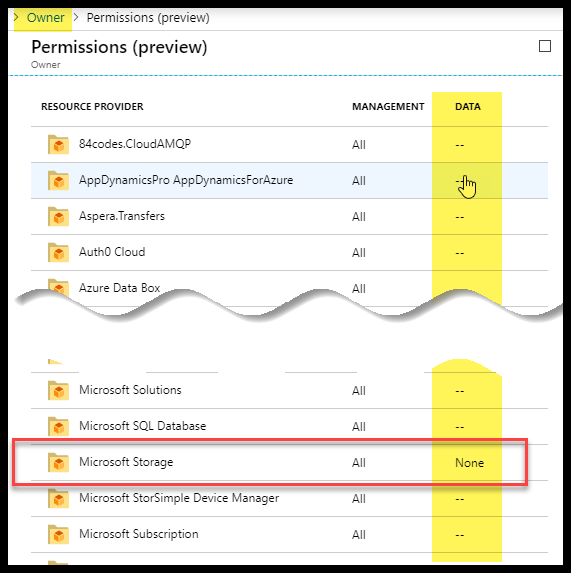
Alice has the Owner role on the Subscription and her role gives her permission to the storage account that holds the blob containers. She has full management rights to all of the stuff in the storage account, including the blob containers themselves (blue area in the picture above). She doesn't have rights to look at the individual blobs within the blob containers however. Her role has entries in the Management actions ("Actions / NotActions" sections of the definition), but she doesn't have any entries in the Data actions ("DataActions / NotDataActions" sections).
Bob has the Storage Blob Data Contributor role which allows him to see the blob containers in the storage account as well as access the individual blobs within the blob containers.
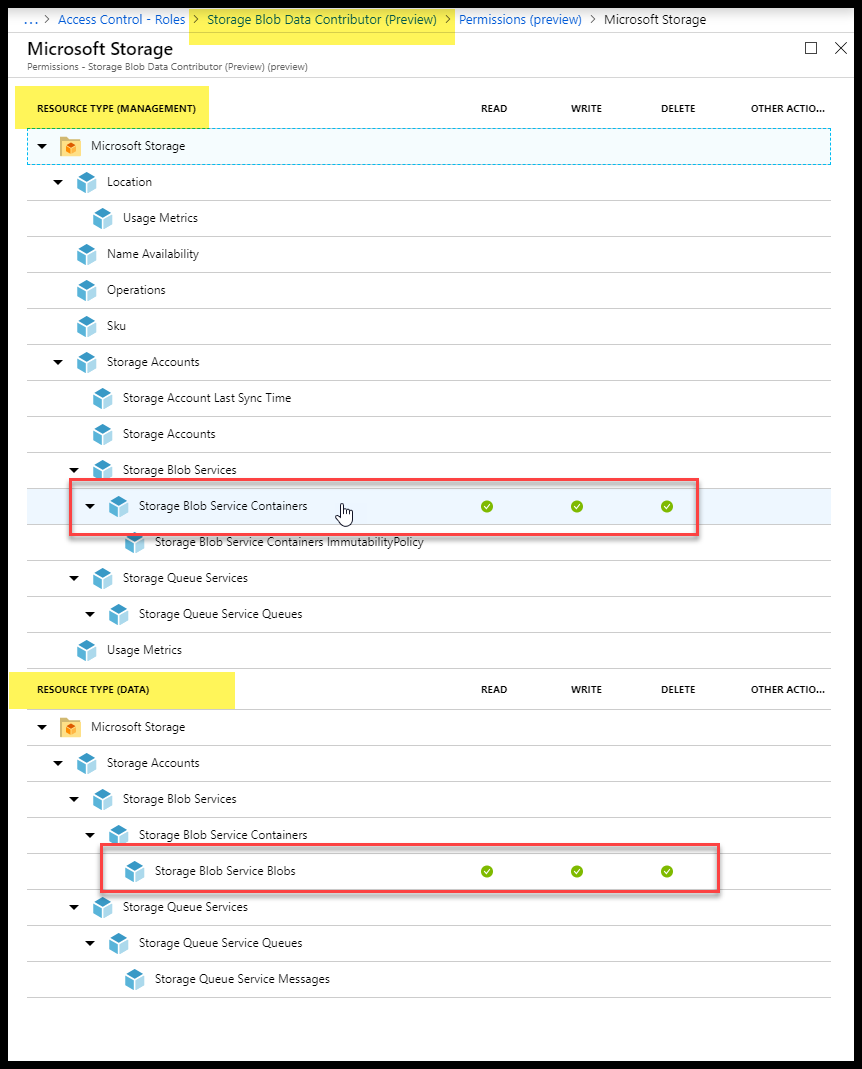
Important: If someone has a Role with a given resource in the NotDataActions section, but has a different role with that same resource in the DataActions section then that person will have access to that data. The NotDataActions section is not a Deny setting.
More info:
Understanding Role Definitions in Azure RBAC - Management and Data Operations
Governance in Azure



Comments